Mirrorculous is a mirror of the future that intelligently assists users by offering suggestions and reminders for day to day tasks . It has the ability to synchronize with your calendar/ smart phone and analyze your schedule . Based on its cloud based artificial intelligence and face detection technology it suggests grooming tips that are relevant to the occasion. It can be used by multiple users and maintain user profiles based on facial recognition.
Outcome
Project Description
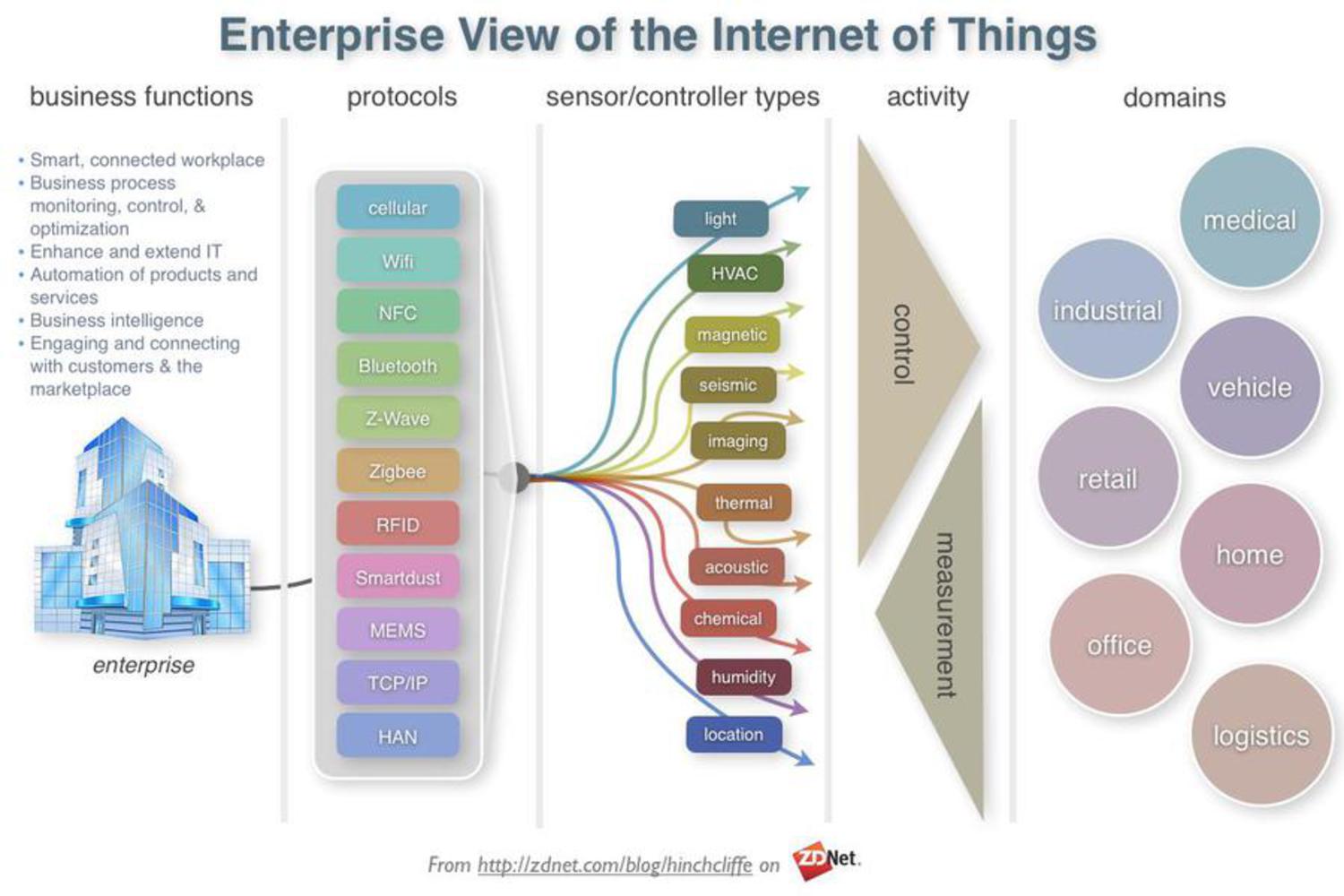
British entrepreneur Kevin Ashton first coined the term IOT in 1999 while working at Auto-ID Labs (originally called Auto-ID centers, referring to a global network of objects connected to radio-frequency identification, or RFID).Typically, IoT is expected to offer advanced connectivity of devices, systems, and services that goes beyond machine-to-machine communications and covers a variety of protocols, domains, and applications.
The concept of a network of smart devices was discussed as early as 1982, with a modified Coke machine at Carnegie Mellon University becoming the first internet-connected appliance, able to report its inventory and whether newly loaded drinks were cold.
Interconnected products have seeped into our daily lives , every device we interact with in our day to day activities has the potential of communicating with the internet . This is beneficial in many ways , to begin with , it provides the user with analytical data about their behaviors and helps in making better decisions there by increasing efficiency. However this raises concerns about data security and privacy.This could lead to compromising personal identity and behaviors. Through our project we have attempted to portray what happens when sensitive information falls in wrong hands.
Mirrorcullus is a smart mirror that depicts a scenario where in it performs the role of a personalized assistant that syncs with your calendar and learns about your schedules . Based on cloud intelligence it gets smarter and establishes patterns about user behavior. Its function is to provide settle nudges to the user such as personal grooming tips for an interview, reminders for meetings , dates or important occasions.
Design Recommendations
Security tools need to be applied directly to the connected devices. "The IoT and its cousin BYOD have the same security issues as traditional computers," says Randy Marchany, CISO at Virginia Tech University and the director of Virginia Tech's IT Security Laboratory. "However, IoT devices usually don't have the capability to defend themselves and might have to rely on separate devices such as firewalls [and] intrusion detection/prevention systems. Creating a separate network segment is one option." In fact, the lack of security tools on the devices themselves or a lack of timely security updates on the devices is what could make securing the IoT somewhat more difficult from other types of security initiatives, Marchany says. "Physical security is probably more of an issue, since these devices are usually out in the open or in remote locations and anyone can get physical access to it," Marchany says. "Once someone has physical access to the device, the security concerns rise dramatically."
Security needs to be built in as the foundation of IoT systems, with rigorous validity checks, authentication, data verification, and all the data needs to be encrypted. At the application level, software development organizations need to be better at writing code that is stable, resilient and trustworthy, with better code development standards, training, threat analysis and testing. As systems interact with each other, it's essential to have an agreed interoperability standard, which safe and valid. Without a solid bottom-top structure we will create more threats with every device added to the IoT. What we need is a secure and safe IoT with privacy protection, it is a tough trade off but not entirely impossible.
References :
Epic org - https://epic.org/privacy/internet/iot/
Wikipedia - https://en.wikipedia.org/wiki/Internet_of_Things
You can upload files of up to 20MB using this form.